Security vs. Compliance
Introduction
In cybersecurity discussions, "security" and "compliance" are often used interchangeably—but this confusion can be costly. While deeply related, they serve different purposes and solve different problems. Understanding this distinction is essential for building a mature security programme that delivers real business value rather than becoming a perceived cost centre.
What is Compliance?
Compliance is the act of adhering to a defined set of rules. The key word here is defined—it's a baseline of minimum standards set by an external party, whether that's a regulator (APRA), a customer (contract), or an industry body (SOC2 or ISO 27001).
Why Compliance Matters
Compliance serves three main business functions:
- Regulatory: Legal mandates you must follow, such as the Australian Privacy Act or APRA standards. Non-compliance leads to fines and legal penalties.
- Contractual: Requirements imposed by partners and customers. For example, a major client may refuse to do business without a SOC 2 report.
- Marketing: Compliance as a badge of trust. An ISO 27001 certification tells the market you're serious about security and directly enables sales.
The Limitation
Compliance is a "point-in-time" snapshot. An auditor follows a checklist to verify you meet the standard on that particular day. The problem? An attacker doesn't care about your checklist. You can pass every audit and still suffer a breach.
What is Security?
Security is a continuous, adaptive process designed to protect your business from actual threats. Unlike compliance's static requirements, security assumes you have an active, intelligent adversary actively trying to bypass your controls.
Why Security is Different
This is the core distinction:
- Compliance asks: "Did we pass the audit?"
- Security asks: "Could we stop a breach right now?"
Security is a 24/7/365 discipline focused on:
- Threat modelling: Understanding who is trying to attack you and how
- Detection and response: Finding attackers in your network right now and stopping them
- Culture: Training employees to be a "human firewall" against phishing and social engineering
A classic example: a company passes its PCI DSS audit but fails to detect novel malware on its systems. They passed the "exam" but failed the "real-world test."
The Hybrid Model: Why You Need Both
Many frame this as a battle between "rules" and "risk." The truth? You need both. Security without compliance still exposes companies to legal or contractual risks. Compliance without security is a useless box-ticking exercise, likely more security theatre than effective risk reduction.
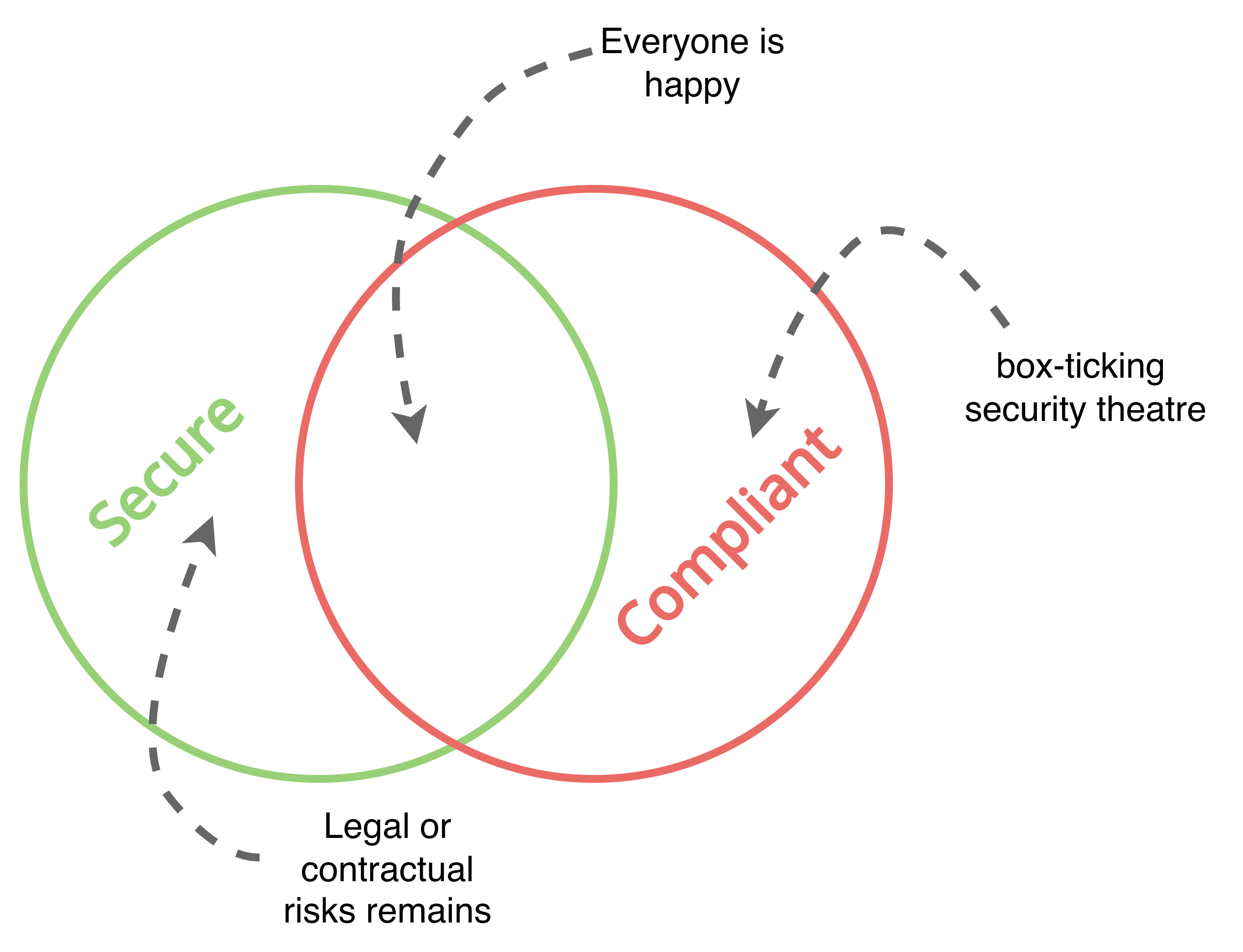
A mature organisation uses a hybrid model:
- Compliance as the baseline: This is your non-negotiable floor—the pass/fail mandates from law and contracts. Meet these requirements with minimum effective effort to unlock business value (like that $30M-client who needs your SOC 2 report).
- Security as risk-based priority: For every decision above that baseline, use risk to prioritise. Focus on what actually protects your business from real threats.
How to Prioritise: Beyond Vague Mathematics
Many organisations get lost trying to quantify cyber risk with spurious precision. You don't need to know the exact pound cost of a breach with 99.9% certainty. You just need to be able to prioritise.
A qualitative, risk-based approach is far more effective. Answer two simple questions:
- What is the impact of this risk? (Low, Medium, High)
- What is the effort to address it? (Low, Medium, High)
Plot every security project onto a simple 9-box grid. Your top priority is always the high-impact, low-effort items—the "quick wins" that deliver the most risk reduction for the least cost. Your lowest priority? Low-risk, high-effort projects that drain budgets for minimal gain.
Conclusion: The Dual Role of Modern Security
A mature security programme plays two complementary roles:
- Business enabler: By efficiently achieving compliance certifications (SOC 2, ISO 27001), it provides the trust and credentials needed to win customers and enter new markets.
- Business defender: By using risk-based security processes, it actively protects the revenue and reputation it helped to enable.
Stop treating security and compliance as the same thing. Use compliance to enable your business and security to protect it.